Request A Quote
- Availability:
- 3-7+ Business Day - ETA

Purchase Protection
Every Order is Protected By BuySafe
Our commitment to sustainability ensures that every purchase supports responsible operations and a healthier planet.
SSL Secure Payment
We make sure your orders are processed as quickly as possible - stocked products are shipped next business day - Vendor direct ship products are processed directly with vendors with vendor leadtime.
Express Shipping
Price Match Guarantee
Your payment is secure
Your privacy and security are our top priority. Our advanced encrypted payment system protects your information during every transaction.

Get expert help
Our team of experienced professionals is always ready to help.
Product Details
Palo Alto PA-7050 Base Chassis Bundle 9HE incl. System Cards, 4x AC- PAN-PA-7050-AC-SYS
Palo Alto PA-7000 Series ML-Powered Next-Generation Firewalls (NGFWs) enable enterprise-scale organizations and service providers to deploy security in high-performance environments, such as large data centers and high-bandwidth network perimeters.
Designed to handle growing throughput needs for application-, user-, and device-generated data, these systems offer amazing performance, prevention capabilities to stop the most advanced cyberattacks, and high-throughput decryption to stop threats hiding under the veil of encryption. Built to maximize security-processing resource utilization and automatically scale as new computing power becomes available, the PA-7000 Series offers simplicity defined by a single-system approach to management and licensing.
Next-Generation Firewall Overview:
Fundamental shifts in the application and threat landscape, user behavior, and network infrastructure have steadily eroded the security that traditional port-based firewalls once provided. Your users are accessing all types of applications using a range of device types, often times to get their job done. Meanwhile, datacenter expansion, virtualization, mobility, and cloud-based initiatives are forcing you to re-think how to enable application access yet protect your network.
Traditional responses include an attempt to lock down all application traffic through an evergrowing list of point technologies in addition to the firewall, which may hinder your business; or allowing all applications, which is equally unacceptable due to increased business and security risks. The challenge that you face is that your traditional port-based firewall, even with bolt-on application blocking, does not provide an alternative to either approach. In order to strike a balance between allowing everything and denying everything, you need to safely enable applications by using business-relevant elements such as the application identity, who is using the application, and the type of content as key firewall security policy criteria.
Key safe enablement requirements:
- Identify applications, not ports. Classify traffic, as soon as it hits the firewall, to determine the application identity, irrespective of protocol, encryption, or evasive tactic. Then use that identity as the basis for all security policies.
- Tie application usage to user identity, not IP address, regardless of location or device. Employ user and group information from enterprise directories and other user stores to deploy consistent enablement policies for all your users, regardless of location or device.
- Protest against all threats—both known and unknown. Prevent known vulnerability exploits, malware, spyware, malicious URLs while analyzing traffic for, and automatically delivering protection against highly targeted and previously unknown malware.
- Simplify policy management. Safely enable applications and reduce administrative efforts with easy-to-use graphical tools, a unified policy editor, templates, and device groups.
Safe application enablement policies can help you improve your security posture, regardless of the deployment location. At the perimeter, you can reduce your threat footprint by blocking a wide range of unwanted applications and then inspecting the allowed applications for threats— both known and unknown. In the datacenter – traditional or virtualized, application enablement translates to ensuring only datacenter applications are in use by authorized users, protecting the content from threats and addressing security challenges introduced by the dynamic nature of the virtual infrastructure. Your enterprise branch offices and remote users can be protected by the same set of enablement policies deployed at the headquarters location, thereby ensuring policy consistency.
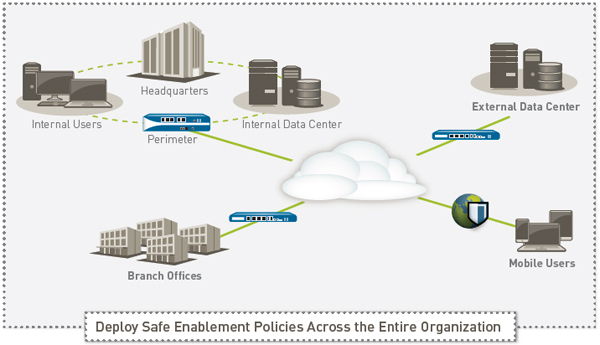
Enabling Applications to Empower the Business
Safe application enablement with Palo Alto Networks™ next-generation firewalls helps you address your business and security risks associated with the rapidly growing number of applications traversing your network. By enabling applications for users or groups of users, both local, mobile, and remote, and protecting the traffic against known and unknown threats, you can improve your security posture while growing your business.
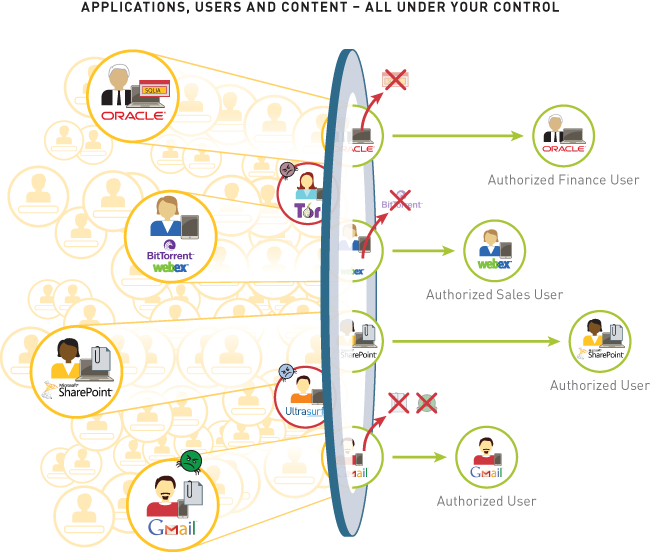
- Classifying all applications, across all ports, all the time. Accurate traffic classification is the heart of any firewall, with the result becoming the basis of the security policy. Today, applications can easily bypass a port-based firewall; hopping ports, using SSL and SSH, sneaking across port 80, or using non-standard ports. App-ID™ addresses the traffic classification visibility limitations that plague traditional firewalls by applying multiple classification mechanisms to the traffic stream, as soon as the firewall sees it, to determine the exact identity of application traversing your network, regardless of port, encryption (SSL or SSH) or evasive technique employed. The knowledge of exactly which applications are traversing your network, not just the port and protocol, becomes the basis for all your security policy decisions. Unidentified applications, typically a small percentage of traffic, yet high in potential risk, are automatically categorized for systematic management— which can include policy control and inspection, threat forensics, creation of a custom App-ID, or a packet capture for Palo Alto App-ID development.
- Integrating users and devices, not just IP addresses into policies. Creating and managing security policies based on the application and the identity of the user, regardless of device or location, is a more effective means of protecting your network than relying solely on port and IP address. Integration with a wide range of enterprise user repositories provides the identity of the Microsoft Windows, Mac OS X, Linux, Android, or iOS user accessing the application. Users who are traveling or working remotely are seamlessly protected with the same, consistent policies that are in use on the local, or corporate network. The combined visibility and control over a user's application activity means you can safely enable the use of Oracle, BitTorrent, or Gmail, or any other application traversing your network, no matter where or how the user is accessing it.
- Protect against all threats, both known and unknown. To protect today's modern network, you must address a blend of known exploits, malware and spyware as well as completely unknown and targeted threats. This process begins by reducing the network attack surface by allowing specific applications and denying all others, either implicitly through a deny-all-else strategy or through explicit policies. Coordinated threat prevention can then be applied to all allowed traffic, blocking known malware sites, vulnerability exploits, viruses, spyware and malicious DNS queries in a single pass. Custom or otherwise unknown malware is actively analyzed and identified by executing the unknown files and directly observing more than 100 malicious behaviors in a virtualized sandbox environment. When new malware is discovered, a signature for the infecting file and related malware traffic is automatically generated and delivered to you. All threat prevention analysis uses full application and protocol context, ensuring that threats are always caught even if they attempt to hide from security in tunnels, compressed content or on non-standard ports.
Deployment and Management Flexibility
Safe application enablement functionality is available in either a purpose-built hardware platform or in a virtualized form factor. When you deploy multiple Palo Alto firewalls, in either hardware or virtual form factors, you can use Panorama, an optional centralized management offering to gain visibility into traffic patterns, deploy policies, generate reports and deliver content updates from a central location.

Application Visibility: View application activity in a clear, easy-to-read format. Add and remove filters to learn more about the application, its functions and who is using them.
Safe Application Enablement: A Comprehensive Approach
Safe application requires a comprehensive approach to securing your network and growing your business that begins with in-depth knowledge of the applications on your network; who the user is, regardless of their platform or location; what content, if any, the application is carrying. With more complete knowledge of network activity, you can create more meaningful security policies that are based on elements of application, user and content that are relevant to your business. The user location, their platform and where the policy is deployed—perimeter, traditional or virtualized datacenter, branch office or remote user— make little or no difference to how the policy is created. You can now safely enable any application, any user, and any content.
Complete Knowledge Means Tighter Security Policies
Security best practices dictate that more complete knowledge of what's on your network is beneficial to implementing tighter security policies. For example, knowing exactly which applications are traversing your network, as opposed to the broader set of traffic that is portbased, enables your administrators to specifically allow the applications that enable your business while blocking, unwanted applications. The knowledge of who the user is, not just their IP address, adds another policy criteria that allows you to be more specific in your policy assignment.
- Using a powerful set of graphical visualization tools, your administrators can gain a more complete picture of the application activity, the potential security impact, and make a more informed policy decision. Applications are continuously classified and as their state changes, the graphical summaries are dynamically updated, displaying the information in an easy-touse, web-based interface.
- New or unfamiliar applications can be quickly investigated with a single click that displays a description of the application, its behavioral characteristics, and who is using it.
- Additional visibility into URL categories, threats, and data patterns provides a complete and well-rounded picture of network activity.
- Unknown applications, typically a small percentage on every network, yet high in potential risk, are categorized for analysis to determine if they are internal applications, as yet unidentified commercial applications, or threats.
Enabling Applications and Reducing Risk
Safe application enablement uses policy decision criteria that includes application/application function, users and groups, and content as a means of striking a balance between business limiting denying of all applications and the high risk alternative of allowing all applications.
At the perimeter, including branch offices, mobile, and remote users, enablement policies are focused on identifying all the traffic, then selectively allowing the traffic based on user identity; then scanning the traffic for threats. Policy examples may include:
- Limit the use of webmail and instant messaging usage to a select few variants; decrypt those that use SSL, inspect the traffic for exploits and upload unknown files to WildFire™ for analysis and signature development.
- Allow streaming media applications and websites but apply QoS and malware prevention to limit the impact on VoIP applications and protect your network.
- Control Facebook by allowing all your users to "browse", blocking all Facebook games and social plugins; and allowing Facebook posting only for marketing. Scan all Facebook traffic for malware and exploits
- Control web-surfing by allowing and scanning traffic to business related web sites while blocking access to obvious non-work related web sites; "coach" access to questionable sites through customized block pages.
- Enforce consistant security by transparently deploying the same policies to all users, local, mobile, or remote, with GlobalProtect™.
- Use an implicit deny-all-else strategy or explicitly block unwanted applications such as P2P and circumventors or traffic from specific countries to reduce the application traffic that introduces business and security risk.
In the datacenter—traditional, virtualized or a combination thereof—enablement examples are focused on confirming applications, looking for rogue applications, and protecting the data.
- Isolate the Oracle-based credit card number repository in its own security zone; control access to finance groups, forcing the traffic across its standard ports, and inspecting the traffic for application vulnerabilities.
- Enable only the IT group to access the datacenter using a fixed set of remote management applications (e.g., SSH, RDP, Telnet) across their standard ports.
- Allow Microsoft SharePoint Administration to be used by only your administration team, and allow access to Microsoft SharePoint Documents for all other users.

Unified Policy Editor: A familiar look and feel enables the rapid creation and deployment of policies that control applications, users and content.

Content and Threat Visibility: View URL, threat and file/data transfer activity in a clear, easy-to-read format. Add and remove filters to learn more about individual elements.
Protecting Enabled Applications
Safe application enablement means allowing access to certain applications, then applying specific policies to block known exploits, malware and spyware – known or unknown; controlling file or data transfer, and web surfing activity. Common threat evasion tactics such as port-hopping and tunneling are addressed by executing threat prevention policies using the application and protocol context generated by the decoders in App-ID. In contrast, UTM solutions take a silo-based approach to threat prevention, with each function, firewall, IPS, AV, URL filtering, all scanning traffic without sharing any context, making them more susceptible to evasive behavior.
Shipping & Return
Return Policy
You need to have a Return Authorization (RA) number before returning any products to HSSL Technologies.
For a hard copy of this form and a shipping label, please include your request in the form below.
You can also request an RA online by submitting an RA Request via email. Once you have provided HSSL Technologies with the appropriate information, we will contact you with an assigned RA number.
Defective or DOA Products
DOA or defective products are returned for REPLACEMENT ONLY with the same product/model. Deviations from this policy may result in a 20% Returns Processing Service Charge.
- Defective products must be in the original factory carton with all original packing materials.
- The Return Authorization number must be on the shipping label, not the carton. Please do not write on the carton.
- Returns must be shipped freight prepaid. Products received freight collect, without an RA number, or not approved for return will be refused.
- Return Authorization numbers are valid for fourteen (14) days only. Products returned after expiration will be refused.
- HSSL credits are based on the purchase price or current price, whichever is lower.
General Return Terms
You may return most new, unopened items within 30 days of delivery for a full refund. We will also pay return shipping costs if the return is a result of our error (e.g., you received an incorrect or defective item).
You should expect to receive your refund within approximately six weeks of giving your package to the return shipper. This period includes:
- 5–10 business days for us to receive your return from the shipper
- 3–5 business days for us to process your return
- 5–10 business days for your bank to process the refund
If you need to return an item, please Contact Us with your order number and product details. We will respond quickly with instructions for returning items from your order.
Shipping Policy
We can ship to virtually any address in the world. Note that there are restrictions on some products, and certain products cannot be shipped to international destinations.
When you place an order, we will estimate shipping and delivery dates based on the availability of your items and the shipping options you select. Depending on the provider, estimated shipping dates may appear on the shipping quotes page.
Please also note that shipping rates for many items are weight-based. The weight of each item can be found on its product detail page. To reflect the policies of the shipping companies we use, all weights will be rounded up to the next full pound.
Has my order shipped?
Click the "My Account" link at the top right hand side of our site to check your orders status.
How do I change quantities or cancel an item in my order?
Click the "My Account" link at the top right hand side of our site to view orders you have placed. Then click the "Change quantities / cancel orders" link to find and edit your order. Please note that once an order has begun processing or has shipped, the order is no longer editable.
How do I track my order?
Click the "My Account" link at the top right hand side of our site to track your order.
My order never arrived.
Click the "My Account" link at the top right hand side of our site to track your order status. Be sure that all of the items in your order have shipped already. If you order displays your Package Tracking Numbers, check with the shipper to confirm that your packages were delivered. If your packages each show a status of "delivered", please contact customer service for assistance.
An item is missing from my shipment.
Click the "My Account" link at the top right hand side of our site to track your order status. Be sure that all of the items in your order have shipped already. If you order displays your Package Tracking Numbers, check with the shipper to confirm that your packages were delivered. If your packages each show a status of "delivered", please contact customer service for assistance.
My product is missing parts.
Click the "My Account" link at the top right hand side of our site to track your order status. Be sure that all of the items in your order have shipped already. If you order displays your Package Tracking Numbers, check with the shipper to confirm that your packages were delivered. If your packages each show a status of "delivered", please contact customer service for assistance.
When will my backorder arrive?
Backordered items are those which our suppliers are unable to predict when they will have more in stock, but as soon as they do, we will be able to ship the item to you.
Warranty
Why Choose HSSL?
We connect businesses with the right technology solutions to power growth, security, and efficiency.

Expertise
Backed by years of industry knowledge, our specialists understand the challenges modern businesses face.

Partnerships
We collaborate with top-tier technology providers to bring you innovative & high-performance products.

End-to-End Support
Our dedicated support ensures your systems stay optimized, secure, and ready for what’s next.

Scalable Solutions
Our adaptive approach ensures your IT infrastructure evolves seamlessly as your business expands.
Expert in IT & Security Solutions
At HSSL, we specialize in delivering cutting-edge IT infrastructure, cloud, and cybersecurity services that empower businesses to thrive in a digital-first world. Our trusted professionals provide reliable insights on:
-
Digital Transformation Strategy
Empowering businesses to adapt and grow through modern, secure, and scalable digital infrastructure.
-
Advanced Cybersecurity
Protecting your organization from digital threats with proactive monitoring and smart security frameworks.
-
Cloud & Infrastructure Management
Optimizing cloud performance and IT operations for seamless scalability and improved business agility.
-
Data Backup & Recovery
Ensuring business continuity through secure data management, automated backups, and rapid recovery solutions.
-
Network & Endpoint Solutions
Delivering secure, high-performance networking systems that keep your business connected and efficient.
-
Technology Consulting
Guiding organizations toward smarter IT investments and solutions that align with their long-term goals.



































