Introduction
Hackers will try just about anything to get you to click on a malicious link.
The key is to make the overall email seem as believable as possible. The more legitimate it seems, the better. The more believable it seems, the better.
The race to get end-users to click on links is on, and creative examples abound.
One tactic that we’re seeing more and more of is using voicemail as a lure to get users to click.
Many corporate phone systems are tied to email—voicemails left on the phone can be available to be listened to via email. Hackers are taking advantage of this by including what appears to be a voicemail recording, but is instead hyperlinked to a malicious page.
In the last two weeks, we saw 1,000 of these attacks.
In this attack brief, Harmony Email researchers will discuss how hackers are disguising credential harvesting links within fake voicemails.
Attack
In this attack, hackers are sending QR codes with conditional routing based on device.
- Vector: Email
- Type: Credential Harvesting
- Techniques: Social Engineering
- Target: Any end-user
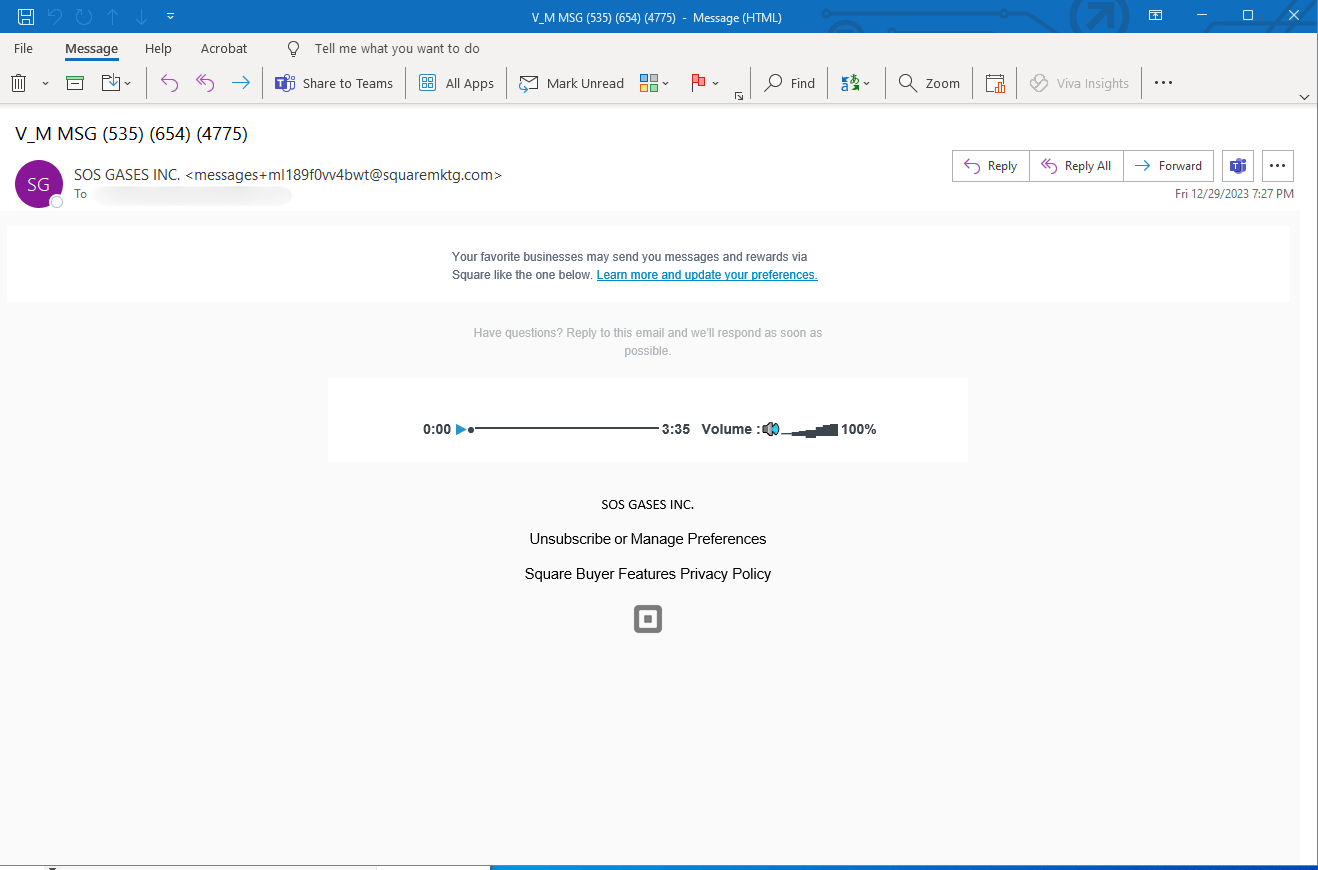
Email Example
The email starts with a subject line that has a phone number. The phone number, if you Google it, is not a legitimate number.
Go further than that, and the email appears to—but does not–come from Square, the payment processor service. It’s a fairly convincing spoof of the brand.
In the email, there’s just what looks like an embedded MP3 player, which would appear to be the voicemail.
When you click on it, however, you get redirected to a webpage, which is actually the credential harvesting page.
Techniques
With the exception of zero-click attacks, which are rising in prominence, hackers need the participation of the user in a successful phishing attack. The user either needs to replay, click on a link, or enter information for an attack to progress.
This focuses the job of the hacker, but it also gives them the opportunity to try new, creative options to induce the participation of their target.
A voicemail may be effective for some users; others might see right through it. By impersonating a well-known brand, and adding a voicemail which most would be curious about, hackers have created an interesting way to get credentials from end-users.
And at the very least, hackers will be able to see the adoption of this technique and adjust their future attacks accordingly.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Implement security that uses AI to look at multiple indicators of phishing
- Implement security that checks and emulates all URLs
- Implement security with multiple layers of protection.
 US Dollars
US Dollars
 United Arab Emirates Dirham
United Arab Emirates Dirham
 Euro
Euro
 British Pound
British Pound
 Turkish Lira
Turkish Lira
 Canadian Dollar
Canadian Dollar
 South African Rand
South African Rand
 Indian Rupee
Indian Rupee
 Brazilian Real
Brazilian Real
 Indonesian Rupiah
Indonesian Rupiah
 Singapore Dollar
Singapore Dollar
 South Korean Won
South Korean Won
 Japanese Yen
Japanese Yen
 Chinese Yuan
Chinese Yuan
 Mexican Peso
Mexican Peso
 Qatari Rial
Qatari Rial
 Saudi Riyal
Saudi Riyal

