Korean researchers have detected a vulnerability in SSDs that allows malware to plant itself directly in an SSD's empty over-provisioning partition. As reported by BleepingComputer, this allows the malware to be nearly invincible to security countermeasures.
Over-provisioning is a feature included in all modern SSDs that improves the lifespan and performance of the SSD's built-in NAND storage. Over-provisioning in essentially just empty storage space. But, it gives the SSD a chance to ensure that data is evenly distributed between all the NAND cells by shuffling data to the over-provisioning pool when needed.
While this space is supposed to be inaccessible by the operating system -- and thus anti-virus tools -- this new malware can infiltrate it and use it as a base of operations.
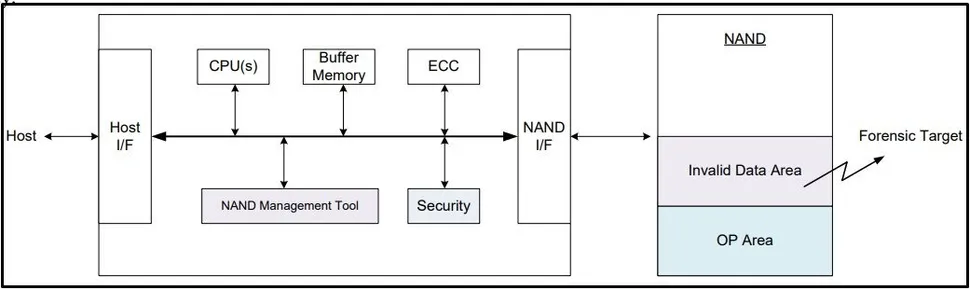
Korean researchers at the Korea University in Seoul modeled two attacks that utilize the over-provisioned space. The first one demonstrates a vulnerability that targets invalid data (data deleted in the OS but not physically wiped) within the SSD. To gain more potentially sensitive data, the attacker can choose to change the size of the over-provisioned data pool to provide additional empty space to the operating system. So when a user goes to delete more data, extra data remains physically intact within the SSD.
SSDs rarely physically delete data, unless it's absolutely necessary, to preserve resources.
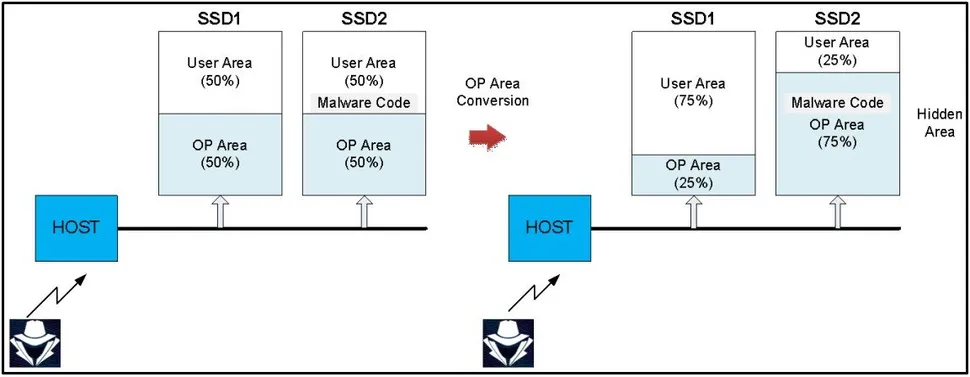
The second one is similar to what was discussed earlier, injecting firmware directly into the over-provisioning pool. In this example, two SSDs are connected as one device, and over-provisioning is set to 50%. When an attacker injects malware into the OP partition of the SSD, they reduce the first SSD's OP range to 25% of the SSD's total size, then increase the OP range of the second SSD to 75%.
This gives the attacker room on the 2nd SSD to inject malware directly into the OP partition while setting the first SSD's OP range to 25%, making it seem like the OP area on both drives has remained unaffected. This is because the OP range for both SSDs combined is still 50%.
The researchers suggest implementing a pseudo-erase algorithm that physically deletes data on an SSD without affecting real-world performance to counter the first attack model.
It is recommended to implement a new monitoring system that can closely watch the over-provisioned size of the SSDs in real-time to counter the second attack model. Plus, access to SSD management tools that can change over-provisioned sizes should have more robust security features against unauthorized access.
Thankfully, these attacks were created by researchers and were not discovered by an actual attack. However, an attack like this could very well happen, so hopefully, SSD manufacturers will start patching these security vulnerabilities quickly before someone gets a chance to exploit them.
 US Dollars
US Dollars
 United Arab Emirates Dirham
United Arab Emirates Dirham
 Euro
Euro
 British Pound
British Pound
 Turkish Lira
Turkish Lira
 Canadian Dollar
Canadian Dollar
 South African Rand
South African Rand
 Indian Rupee
Indian Rupee
 Brazilian Real
Brazilian Real
 Indonesian Rupiah
Indonesian Rupiah
 Singapore Dollar
Singapore Dollar
 South Korean Won
South Korean Won
 Japanese Yen
Japanese Yen
 Chinese Yuan
Chinese Yuan
 Mexican Peso
Mexican Peso
 Qatari Rial
Qatari Rial
 Saudi Riyal
Saudi Riyal

